5 Medical Devices You Didn’t Know Could Be Hacked
Updated: Nov. 05, 2020
A heinous brand of cyber attacks could turn devices designed to keep us healthy into deadly weapons.
The growing threat of hacked medical devices
Hijacked credit card accounts, bank fraud, identity theft—these are all cybercrimes that can leave victims in real financial distress. But as awful as experiencing any of those crimes can be, there is a level of cybercrime that can take things to a new, potentially-fatal, level: medical device hacking.
This threat was fictionalized in a particularly chilling episode of Homeland, where Damian Lewis’ character Brody gave terrorists the serial number of the Vice President’s pacemaker. They used the information to hack into the device, accelerate the VP’s heart rate and kill him.
While this was a Hollywood storyline, the threat is very real. In fact, in 2017 the FDA recalled 465,000 pacemakers (which help control your heartbeat) due to security vulnerabilities that were discovered.
But the threat doesn’t stop at pacemakers. Speaking with CBS News, Suzanne Schwartz, MD, who oversees medical device cybersecurity at the FDA, explained, “Any device can be hacked and that’s often not understood.” Here are some of the medical devices that could be vulnerable to a cyber attack—and these are 20 cyber-security secrets hackers don’t want you to know.
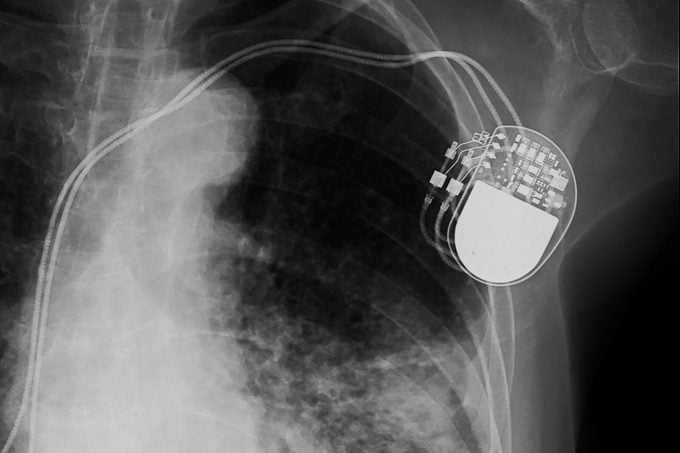
Pacemakers and implanted defibrillators
The aforementioned episode of Homeland may have been based on more fact than fiction. In an interview with Sanjay Gupta on 60 Minutes in 2013, former U.S. Vice President Dick Cheney revealed that in 2007, his implanted heart defibrillator was modified that it so it couldn’t be hacked by terrorists trying to kill him remotely. Cheney’s cardiologist, Jonathan Reiner, MD, explained in the interview, “It seemed to me to be a bad idea for the vice president of the United States to have a device that maybe somebody…might be able to get into, hack into.” Alpine Security reports that “While there have been no reported cases of malicious intent so far, security enhancements for pacemakers and other implantable devices are being addressed by manufacturers and regulatory authorities through firmware updates.” It is a good reminder to take a cybersecurity health check of the connected devices in your home, changing passwords frequently and following this vital computer-security advice.
Drug-infusion pumps
Drug infusion pumps supply patients with a wide diversity of drugs, including insulin, antibiotics, chemotherapy drugs and pain relievers. In 2017, Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) identified multiple vulnerabilities in wireless-connected pumps. According to the ICS-CERT report, “Successful exploitation of these vulnerabilities may allow a remote attacker to gain unauthorized access and impact the intended operation of the pump. Despite the segmented design, it may be possible for an attacker to compromise the communications module and the therapeutic module of the pump.”
Hospital networks
In May of 2017, the computer systems of several major British hospitals crashed causing panic. As reported by the New York Times, experts believe that North Korea perpetrated the attack, but “the government has taken no retaliatory action, uncertain what they can do.” The attack ended when, as the Times describes, a self-taught computer expert named Marcus Hutchins, “spotted a web address somewhere in the software and, on a lark, paid $10.69 to register it as a domain name. The activation of the domain name turned out to act as a kill switch causing the malware to stop spreading.”
Brian Lord, a former deputy director for intelligence and cyber operations at the Government Communications Headquarters in Britain, told the Times, “This was part of an evolving effort to find ways to disable key industries.” He continued: “All I have to do is create a moderately disabling attack on a key part of the social infrastructure, and then watch the media sensationalize it and panic the public.” This is just one of the 50 secrets hospitals don’t want to tell you—but every patient should know.
MRI systems
Britain wasn’t the only target, according to Alpine Security: During the attack, at least one Bayer Medrad medical device in the United States had been hacked. The device is used for monitoring chemicals used in MRI scans. According to Alpine Security, “When they were made aware of the attack, Bayer sent out a Microsoft patch for the imaging equipment and all of their other Windows-based devices.”
Medical records
Healthcare’s cybersecurity problem extends to your medical history, according to tech site Verge. Health records, test results, and prescriptions are stored in the cloud and are susceptible to hackers. Just recently Quest Diagnostics—one of the largest blood-testing companies in the United States—was hacked via their billing collections vendor, and the financial and medical records for more than 12 million patients were exposed. Another risk is that medical information can be intercepted, hijacked, and in worse case scenarios, altered in ways that can lead to misdiagnosis and incorrect treatment plans.
Staying ahead of the hackers
In a public statement released in 2018, FDA Commissioner Scott Gottlieb, MD, stated that “The FDA has been working to stay a step ahead of these changing cybersecurity vulnerabilities, including engaging with external stakeholders. In this way, we can help ensure the health care sector is well positioned to proactively respond when cyber vulnerabilities are identified in products that we regulate.” Medical devices aren’t the only things vulnerable to attack: Here are 17 everyday things vulnerable to hackers.